By Nancy Peaslee
We’ve all seen the headlines: Heightened monitoring of malicious cybersecurity activity in response to global events. Increased ransomware attacks and security breaches. Data leaks of sensitive information.
Your agency’s security operations center has been set up to monitor cybersecurity threats – but is it optimized to predict and prevent cyber vulnerabilities? Is it automated with real-time alerts? Is it synthesizing data so that you can make critical decisions quickly?
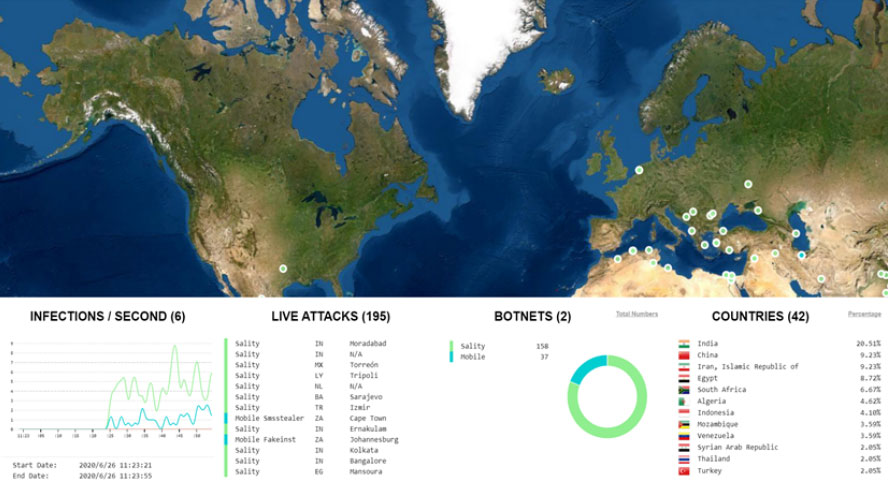
Utilizing machine learning tools, patterns of network attack domains are detected and monitored to identify domain generated algorithm (DGA)/Botnet domains in conjunction with Splunk.
Here are signs that your government agency may need to improve your security operations center:
- Incomplete Picture – Your operations center has a number of powerful tools, but may not have a comprehensive dashboard that helps you see the big picture. Ask yourself, do you have an intuitive dashboard of meaningful data? Can you see trends from combined data and predict behaviors?
- Data in Multiple Systems – You may be pulling data from multiple, disparate tools that don’t talk to one another or perhaps you’re running unique queries in each tool. You may even have different team members assigned to scrutinize system logs, patching requirements, and specific vulnerabilities. This approach leaves your organization open to significant security risks.
- Manual Reporting – When it comes time to pull out the most meaningful information, are you manually aggregating data? Are you struggling with customizing reports for different audiences? Perhaps you’re spending precious time tailoring reports to executives? Cyber attackers work quickly. A robust dashboard tailored to the data your audience needs at a glance to make decisions is vital.
- Lack of Data Integration – Successful security operations centers correlate data, draw conclusions, predict behaviors, and alert relevant team members to potential threats. Perhaps you have a security operations dashboard that promised a lot, but is falling short. It is key to see relationships between data from different tools in real-time so you can identify trends and predict security vulnerabilities.
All of these are easily solved by improving your security operations dashboard to achieve a comprehensive, real-time view of your data. Aggregating data from multiple sources into one place, the dashboard provides leaders and security teams the “big picture” so you can make decisions to shut down attacks, malware, or phishing events faster and proactively predict threats and reduce vulnerabilities.
7 Steps to Improving Your Security Operations Dashboard
Below, we’ve outlined a comprehensive approach to enhancing your security operations dashboard but we realize every government agency is at a different stage with security operations.
1. Define Your Security Profile
You’ll want to begin by defining your security environment – not just events within each tool – to build a common operating picture that reflects your organization’s mission. Review your IT assets and the sensitivity of the data (for example, financial data needs higher security than publicly available data). Conduct a scan to verify what’s on the network and which tools you’re using. Next, look at your people, including who may need further cybersecurity training and who has admin privileges and service account permissions.
2. Develop a Security Baseline
To create a cybersecurity baseline, get started with a vulnerability scan and analysis of your logs. Then determine your current level of risk compared to your organization’s overall risk tolerance. Assess what information is most meaningful for making security decisions and evaluate who needs access and alerts under which threat scenarios.
3. Establish and Improve Security Processes
Establish data security processes aligned with your organization’s risk management tolerance and in compliance with cybersecurity and privacy requirements. This is a big task, so plan ongoing refinements to continually improve your security processes. Start with addressing gaps and vulnerabilities. Consider ways to minimize organizational risks and ensure systems are adequately protected. Establish a configuration management process for iterative refinements to do things more efficiently, effectively, and fine-tune as you go.
4. Survey Audience Needs
Often, the key to an effective security operations dashboard is that it’s tailored to each audience’s role. Get started by thinking about each audience type and which data they need to make the security decisions they’re responsible for. Once you’ve prioritized the data and permission levels each audience needs, you’ll create a unique dashboard tailored to each role.
How security operations dashboards may be customized for specific audiences:
- Executive dashboard: Presents a high-level summary of the organization’s security posture, cybersecurity trends, cybersecurity health, and overall threat level. Features visual alerts and the ability to drill down into details.
- Systems admin dashboard: Offers a high-level summary of all the organization’s systems – servers, switches, routers, firewalls, and workstations – and any impacts on system performance. Displays visual alerts based on the level of severity and features ability to drill down into each system.
- Security admin dashboard: Presents high-level summary of cybersecurity trends, incidents, vulnerabilities, and risk level. Visual alerts are categorized by severity level. Includes details such as recommended remediation steps, common vulnerabilities and exposures (CVEs), available patches, and specific vendor information and tools.
- Security Help Desk dashboard: Offers details on cybersecurity incidents, incident resolution, incident age, incidents per analyst, and incidents per technology type.
5. Evaluate New Tools or Capabilities
There is no such thing as “finished” in security operations – threats morph and change, and your system must adapt. After evaluating audience needs, you may identify new requirements that go beyond your existing tools and equipment. It pays off to have a disciplined approach to evaluating new tools, starting with detailed requirements. Research and compare potential new tools or equipment. Conduct a cost analysis to prioritize the most cost-effective solution. Then, plan out next steps to implement, test, and launch new tools or equipment in your environment.
You may want to consider vulnerability scanners and a variety of new tools that help you collect and analyze system logs, tightly control authentication and access, automate continual monitoring, profile adversaries, do reconnaissance, and understand vulnerabilities the way “threat actors” look at them.
6. Configure and Tailor Your Dashboard
After you’ve prioritized the data needed per audience, you’ll begin to configure and tailor your dashboard to track leading indicators for cybersecurity incidents, events, threats, and vulnerabilities. You may need to use AI and predictive analytics tools to help you analyze, aggregate and correlate data from multiple sources so it prioritizes the highest security risks into a common operating picture. You’ll need to determine how data will be stored and kept secure as well as set key performance indicators (KPIs) for each user type. And you’ll want to plan out automated alerts for critical security issues – prioritizing the highest security risks so leaders can make timely decisions.
What is displayed in a security operations dashboard?
A security operations dashboard is customized to each organization but usually displays:
- Overall threat level and high-level summary of security risks, trends and vulnerabilities
- Authentication errors, unauthorized access, and non-compliant devices
- Attacks against the system, malware, or phishing events
- Cybersecurity events and incidents that occurred
- Visibility into the effectiveness of security measures and risks by severity level
7. Plan for Monitoring and Reporting
Look at how best to use existing and new tools to continuously monitor your systems, networks and data – setting up automated scans, reviews, and alerts. Plan out reporting on the current state of security operations. Your metrics should reveal whether you are meeting the requirements of your security baseline. What is your mean time to patch? How long does it take to detect and respond to potential incidents? What is the average window of exposure? Your reports should help you intimately understand the health of your data, devices, and systems.
Looking to understand your cyber threat landscape? Improve incident response? Assess vulnerability management? Graham Technologies helps government agencies build dashboards that correlate data to display meaningful trends and predictions. Our GTech Labs data scientists use AI, predictive analytics, and data integration techniques to consolidate data into meaningful datasets and build more intuitive dashboards that accelerate decision making. Our cybersecurity experts work daily to manage security operations centers, improve security processes, protect against vulnerabilities, and automate monitoring and alerts to protect your systems from security events and threats.
Contact us today to learn how Graham Technologies can help your government agency improve your security operations dashboard.
